This section describes how to set the IEEE802.1X authentication.
For IEEE802.1X, the RADIUS server requires user authentication from the supplicant (machine) when connecting to a network. EAPOL (EAP over LAN) is used for communication between the supplicant and the authenticator (LAN switch) that performs access control of the terminal based on the authentication results. Authentication information is managed collectively with the RADIUS (Remote Authentication Dial In User Service) server, and then the supplicant is authenticated. Invalid access can be prevented because this authentication method permits only supplicants authenticated by the RADIUS server to connect to the network via an authenticator. The authenticator blocks communication from supplicants not authenticated by the RADIUS server.
The machine supports the following methods of authentications:
|
IMPORTANT
|
|
You cannot set the EAP-TLS method and the EAP-TTLS/PEAP method at the same time.
|
For the EAP-TLS method, authentication is performed by issuing a digital certificate bilaterally to both the client and the RADIUS server. The key pair and client certificate sent from the machine are verified using the CA certificate on the RADIUS server. The server certificate sent from the RADIUS server is verified using the CA certificate on the client (the machine). The CA certificate used to verify the server certificate must be registered. For information on installing the CA certificate file using the Remote UI, see "Installing a CA Certificate." For information on registering the installed CA certificate file, see "Registering a CA Certificate File Installed from a Computer."
Also, the settings for the user login name (to be authenticated by IEEE802.1X authentication) and the password, as well as the settings for the key pair (in PKCS#12 format) and the client certificate are necessary to use EAP-TLS with the machine. After installing the key pair file and client certificate file using the Remote UI (see "Installing a Certificate File"), set the key pair and client certificate for EAP-TLS as the default key with the control panel of the machine.
For the EAP-TTLS method, only the RADIUS server issues a digital certificate. The server certificate sent from the RADIUS server is verified using the CA certificate on the client. The CA certificate used to verify the server certificate must be registered. For information on installing the CA certificate file using the Remote UI, see "Installing a CA Certificate." For information on registering the CA certificate file installed, see "Registering a CA Certificate File Installed from a Computer."
Furthermore, the name of the user/login user to be authenticated with IEEE802.1X authentication and the password need to be set to use EAP-TTLS with the machine.
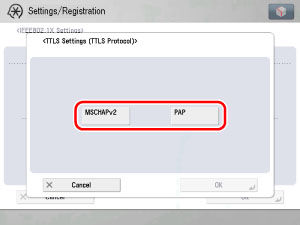
The user can select two types of internal authentication protocol supported by EAP-TTLS: MS-CHAPv2 (Microsoft Challenge Handshake Authentication Protocol Version 2), or PAP (Password Authentication Protocol). You cannot set both MS-CHAPv2 and PAP simultaneously.
For the PEAP method, only the RADIUS server issues a digital certificate. The server certificate sent from the RADIUS server is verified using the CA certificate on the client. The CA certificate used to verify the server certificate must be registered. For information on installing the CA certificate file using the Remote UI, see "Installing a CA Certificate." For instructions on registering the installed CA certificate file, see "Registering a CA Certificate File Installed from a Computer."
Furthermore, the name of the user/login user to be authenticated with IEEE802.1X authentication and the password need to be set to use PEAP with the machine.
The only internal authentication protocol supported by PEAP is MS-CHAPv2.
This section describes how to select the IEEE802.1X authentication method.
1.
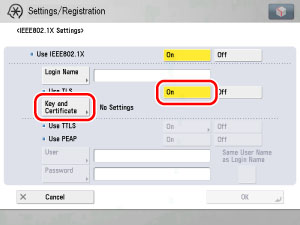
Press [IEEE802.1X Settings] on the Network screen → select [On] for <Use IEEE802.1X>.
|
IMPORTANT
|
|
If you set <Use IEEE802.1X> to 'On', the machine will not enter a complete Sleep mode.
|
2.
Select the IEEE802.1X authentication method on the IEEE802.1X Settings screen.
Register the CA certificate (see "Registering a CA Certificate File Installed from a Computer") in advance. If setting the EAP-TLS method, also install the key pair file and the client certificate file (see "Installing a Certificate File").
Select [On] for <Use TLS> → press [Key and Certificate].
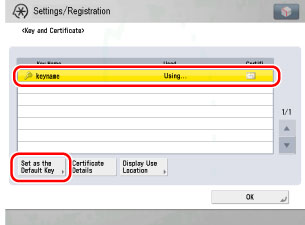
Select the key pair you want to use → press [Set as the Default Key] to register the key pair and client certificate to use for EAP-TLS.
|
IMPORTANT
|
|
You cannot specify 'Device Signature Key' (used for key pairs for adding digital signatures to PDFs or XPSs) or 'AMS' (used for key pairs for access restrictions) as the name for the key pair.
You can check the content of a certificate by selecting a key pair on the Key and Certificate screen, and pressing [Certificate Details]. On the Certificate Details screen, you can press [Certificate] to verify the certificate.
You can check what a key pair is being used for by selecting a key pair with 'Used' displayed for <Status> on the Key and Certificate screen, and pressing [Display Use Location].
|
Enter the name of the user to be authenticated by IEEE802.1X authentication in [Login Name], and the specified login user password in [Password].
Select [On] for <Use TTLS>.
Select the internal authentication protocol to use.
|
IMPORTANT
|
|
You cannot set both MS-CHAPv2 and PAP simultaneously.
|
If a login user wants to be authenticated, they must press [Same User Name as Login Name] and enter their login name in [Login Name] and the specified login user password in [Password]. If users other than login users want to be authenticated, they must enter their user name in [User] and the specified user password in [Password].
Select [On] for <Use PEAP>.
If a login user wants to be authenticated, they must press [Same User Name as Login Name] and enter their login name in [Login Name] and the specified login user password in [Password]. If users other than login users want to be authenticated, they must enter their user name in [User] and the specified user password in [Password].